
Microsoft Entra ID Authentication Setup for PaperSaveCloud™
PaperSave 7.0
3150 SW 38th Avenue,
4th
Floor, Miami, Florida 33146. USA
![]() 877
727 3799
877
727 3799
![]()
Contents
2 Azure AD Authentication Setup for PaperSaveCloud
2.1.1 Obtaining the Microsoft Entra ID's Directory ID
2.1.2 Obtaining the Object ID of an Active Directory Group (Optional)
2.1.3 Consents required post PaperSaveCloud tenant deployment
1 Introduction
When using Microsoft Entra ID based authentication, PaperSave will rely on it to provide all Identity Management. That means that your PaperSaveCloud tenant will be authorized for access only by the specific Microsoft Entra ID directories that you specify can access PaperSave. You can also filter access to PaperSave to only specific groups within Microsoft Entra ID. Basic user and group management tasks such as resetting passwords will be done within Azure AD. Authorization and or other PaperSave specific functions (such as adding tags to users or configuring their notification preferences) are still performed within PaperSave’s User and Group management module. However, the users listed within that module will come from Active Directory and you won’t be able to use that module to add/delete new users/groups, reset passwords, change names, and other basic identity management features.
2 Microsoft Entra ID Authentication Setup for PaperSaveCloud
This section describes the details, parameters, and decisions that our team will need from you to configure a PaperSave tenant to use Microsoft Entra ID authentication as well as the steps that you will need to perform as a prerequisite to and to complete the configuration. It also includes information about the permissions required after the tenant deployment.
Note: The steps below are recommended to be followed by only those Clients who wish to use PaperSaveCloud with Microsoft Entra ID Authentication.
Steps:
Obtaining the Microsoft Entra ID's Directory ID
Obtaining the Object ID of an Active Directory Group (Optional)
Consents required post PaperSaveCloud tenant deployment
2.1 Pre-requisites
PaperSaveCloud supports the following types of Microsoft Entra ID users:
· Microsoft Entra ID users
· Local AD users synchronized with Microsoft Entra ID using Password synchronization
The following pieces of information are pre-requisites for our provisioning team to properly deploy a tenant that uses Microsoft Entra ID Authentication:
· Obtaining the Microsoft Entra ID's Directory ID
·
Obtaining the Object ID of
an Active Directory Group (Optional)
Once the Microsoft Entra ID is ready (or local AD is synchronized with Microsoft Entra ID), the Azure domain name, Microsoft Entra ID’s directory ID, and object ID of AD groups should be provided to the PaperSaveCloud operations team, as described in the sections below.
2.1.1 Obtaining the Microsoft Entra ID's Directory ID
To prevent any unauthorized access from happening we will need your Microsoft Entra ID’s Directory ID so that it can be whitelisted for your PaperSaveCloud tenant.
Follow the steps below to get your Microsoft Entra ID’s Directory ID:
· Navigate to https://portal.azure.com
· Once within the portal, click on Microsoft Entra ID as shown below:
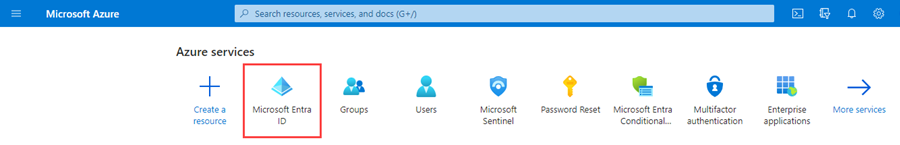
· Now, click on Properties as shown below:
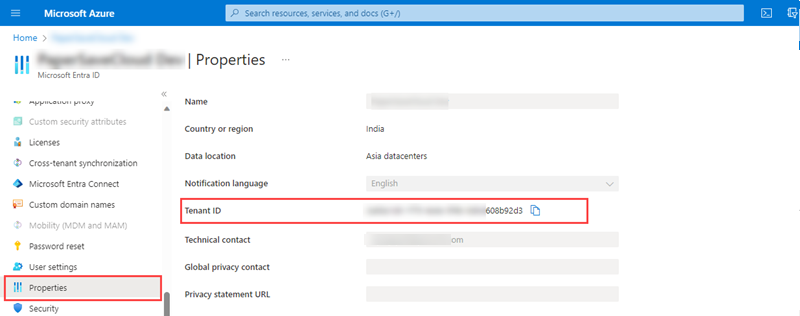
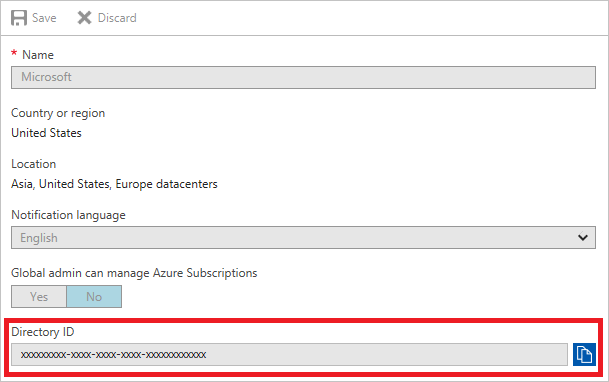
· Click on the copy button next to the directory ID text box and send it to your PaperSave implementation contact.
2.1.2 Obtaining the Object ID of an Active Directory Group (Optional)
This step is only required if you would like to limit access to PaperSave to specific groups. If you don’t provide this filter, then all users within your Microsoft Entra ID will be available to use PaperSave (Note that PaperSave security may be utilized to restrict document and function access). This filter can be added at any time by contacting PaperSave support.
Follow the steps below to obtain an Microsoft Entra ID group’s Object ID.
· Navigate to https://portal.azure.com
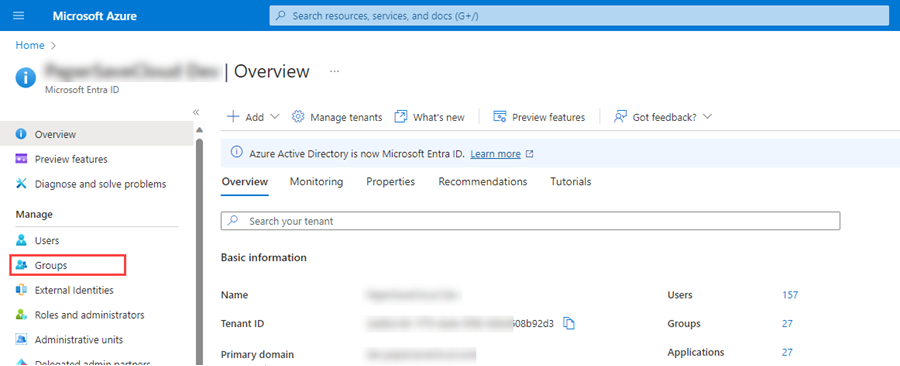
· From the portal, click on “Microsoft Entra ID” as shown below:

· Click on “Groups”, as shown below:
· Select and click on the AD group that should be allowed to access PaperSaveCloud.
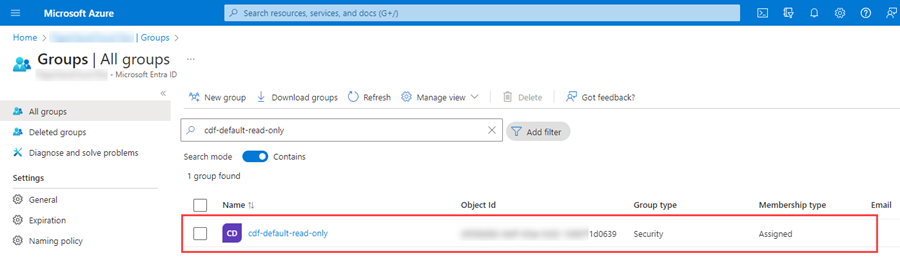
·
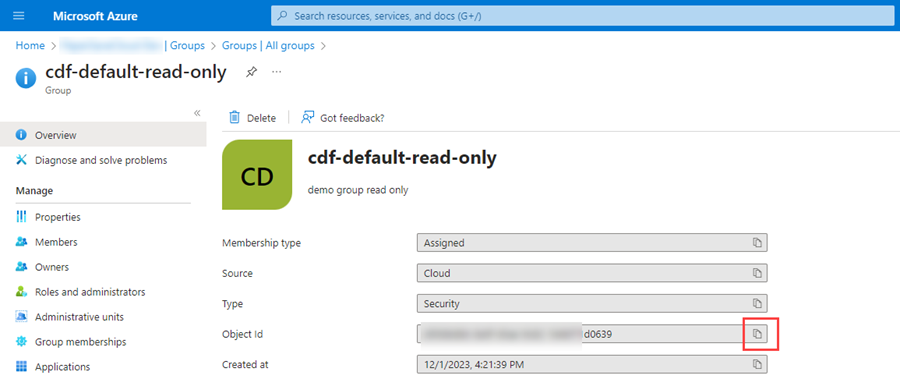
Now, click on copy button next to the “Object ID” text box and
send it to the PaperSaveCloud operations team.
Note: This information is used to configure the PaperSaveCloud tenant. Refer to the Consents required post PaperSaveCloud tenant deployment section to view the list of permissions required from the clients and their purposes.
2.1.3 Consents required post PaperSaveCloud tenant deployment
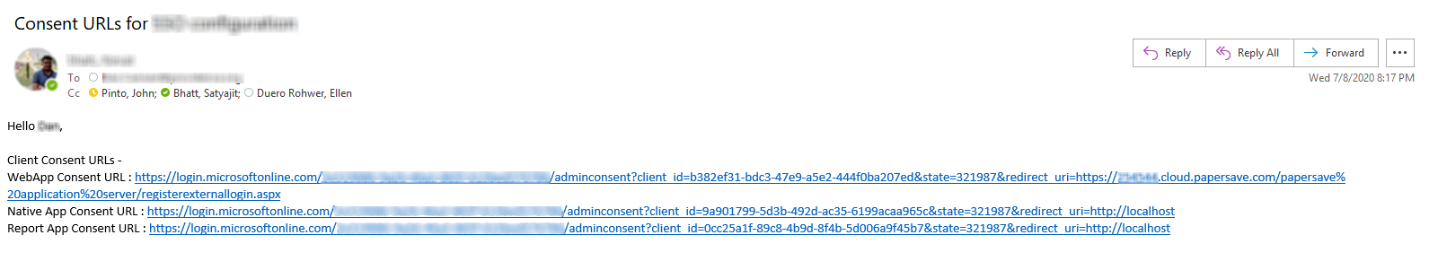
Once the PaperSaveCloud tenant is deployed, an email with the three Consent URLs will be sent to the client, as shown below:
Note: The consents should be granted by the user who has Global Admin rights on the Microsoft Entra ID.
Now, the PaperSaveCloud client will receive below-mentioned Consent URLs in an email. These Consent URL links should be accessed in the same sequential order available in the email.
|
Consent URL |
Description |
|
WebApp Consent URL |
To grant the permissions mentioned in the next table. |
|
Native App Consent URL |
To provide user impersonate permission on WebApp Consent URL to PaperSave. |
|
Report App Consent URL |
To access the report from PaperSave tenant. |
Note:-
1. When you click on WebApp Consent URL, it will redirect you to the PaperSave Application System Start Page.

2. Native App and Report App Consent URLs will get resolved in PaperSaveCloud client’s local host, unlike WebApp Consent URL. Generally, it will display the IIS page after these (Native App and Report App) URLs are successfully resolved.
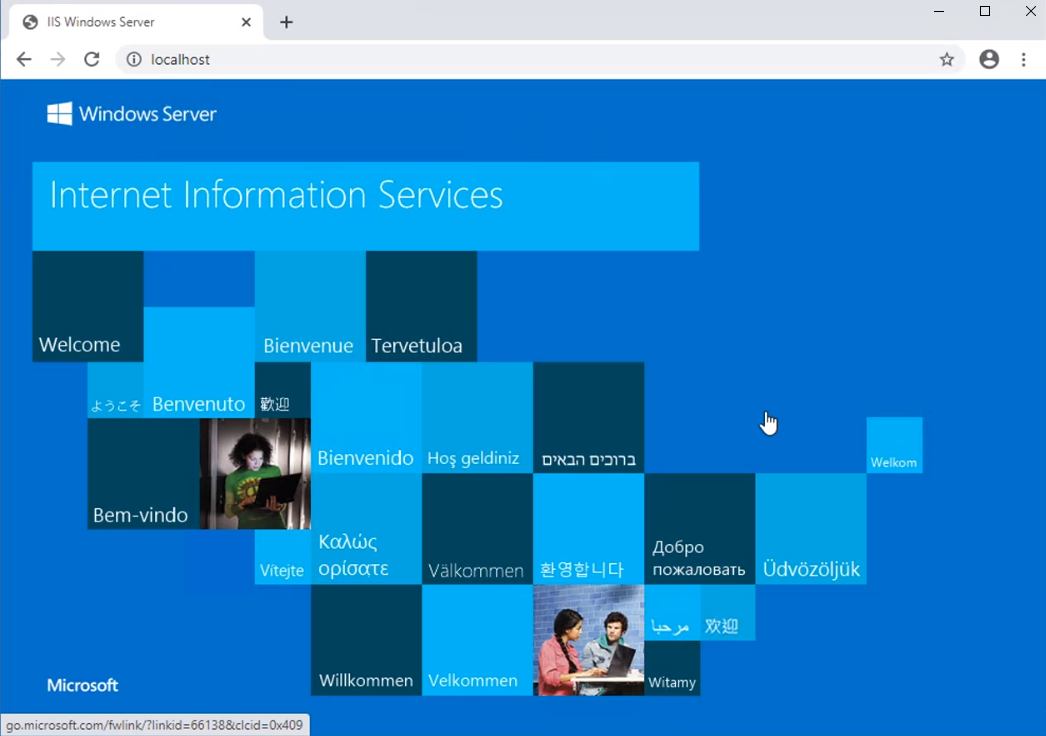
3. In case IIS is not installed on the client's machine, then a blank page will be displayed, but still the required access will be provided.
|
Permission |
Purpose |
|
Sign in and read user profile |
To allow PaperSave to sign-in to Microsoft Entra ID to read the basic details like tenant ID, tenant display name, and verified domains. |
|
Read all users' basic profiles |
To allow PaperSave to read the basic user profile details like display name, first name, last name, profile photo, and email address. |
|
Read directory data |
To allow PaperSave to read the data such as users and groups from the directory. |
Once, the client clicks on all the consent links and provide required permissions, they could login into PaperSave tenant with their Microsoft Entra ID user credentials.